Gatekeeper is a security component, present on every macOS version since macOS X 10.7 Lion. It will verify each application before running them. Depending of your settings, it will allow only applications from the Mac App Store or signed by Apple certified developers. But using a specific command line, it can’t be totally disabled.
SIP, or System Integrity Protection, will protect the core folders of the system. It has been introduced with macOS X 10.12 El Capitan. It will prevent unsigned kexts to install, code injection in processes and modification of system files. You can find more informations here. Unlike Gatekeeper, SIP can only be modified in recovery. We can see it when using the command csrutil :
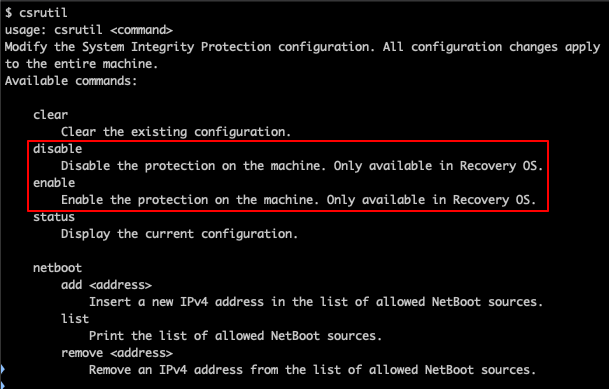
Users can disable it if they are administrators of their computer. As I prefer to protect than repair, I created policies to enable it back.
Smart groups
We need first to detect the computers with Gatekeeper or SIP disabled. We will create two smart groups based on native attributes provided by Jamf.
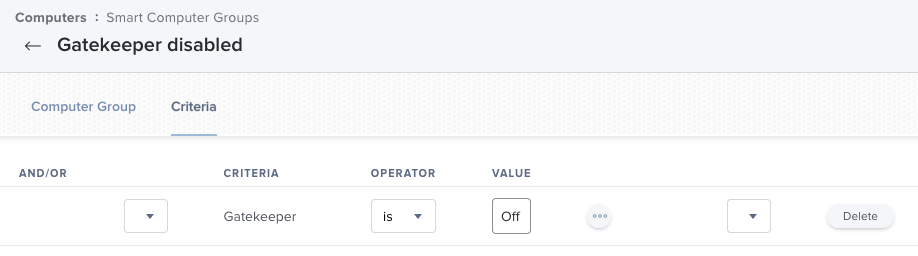
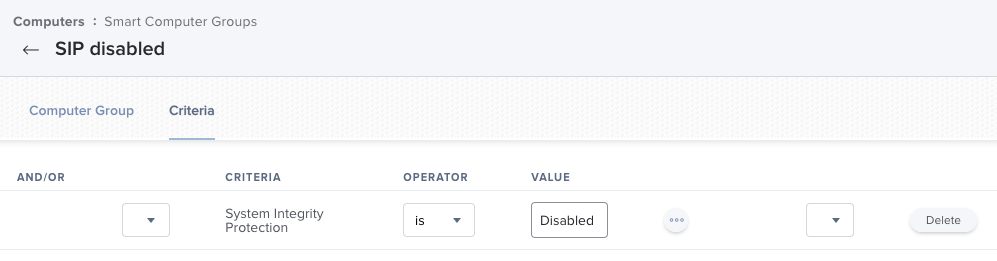
Policies
Gatekeeper
Create a policy and set a trigger to Recurring check-in and a frequency of Once every day.
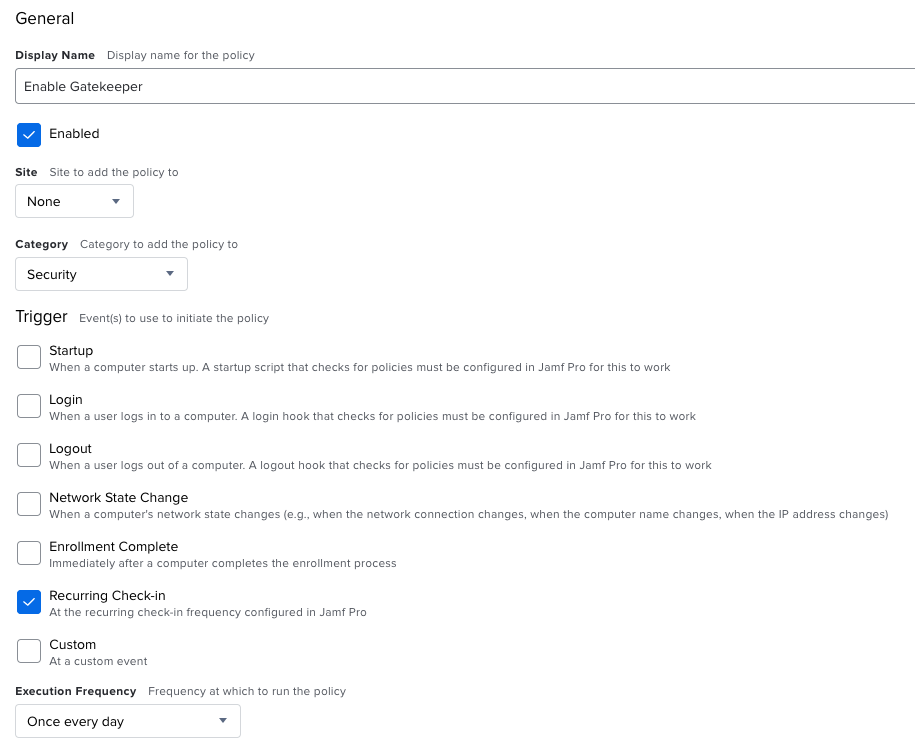
In Files and Processes, add the command spctl –master-enable in Execute Command field

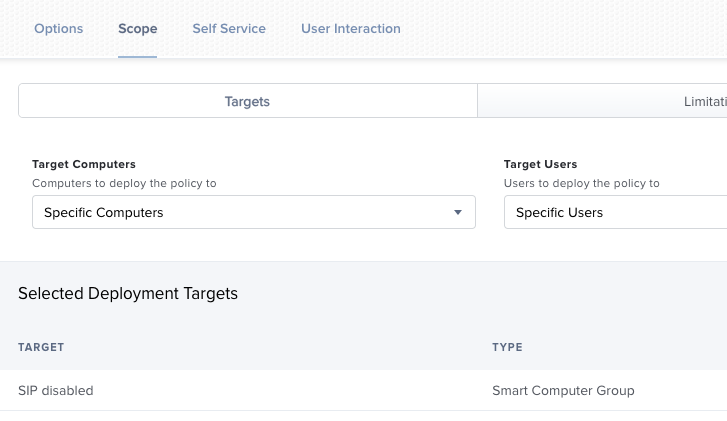
Set the scope to the smart group we have created
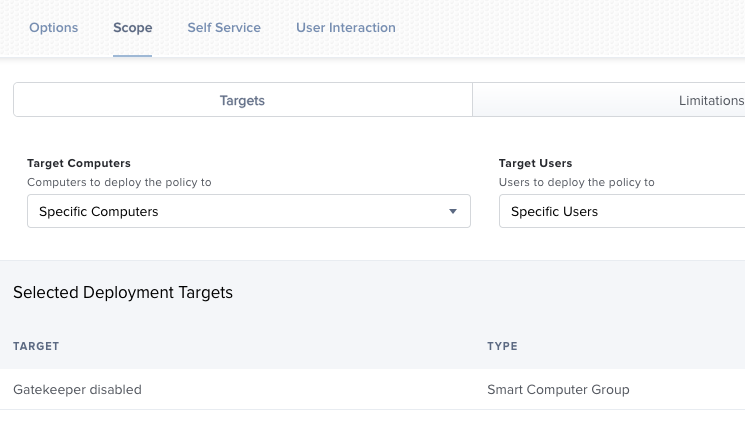
You’re done ! You can add an Inventory Update if you want to have your smart group updated as soon as the policy is executed. Now let’s see for SIP.
SIP
Create another policy and set a trigger to Recurring check-in and a frequency of Once every day, just like Gatekeeper.
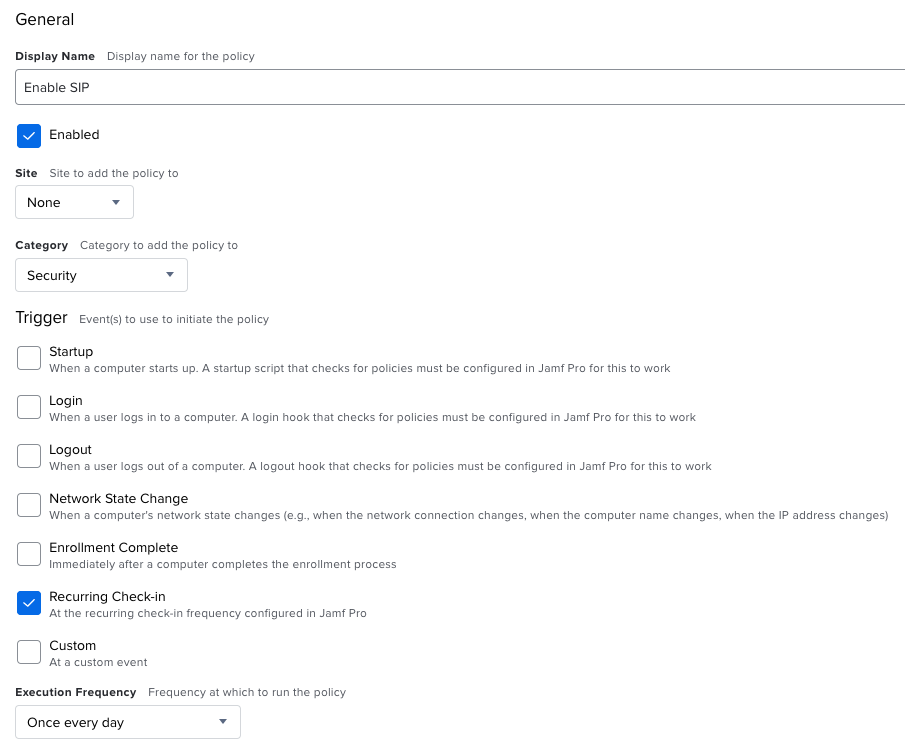
In Files and Processes, we will use the command csrutil clear, to reset the SIP status.
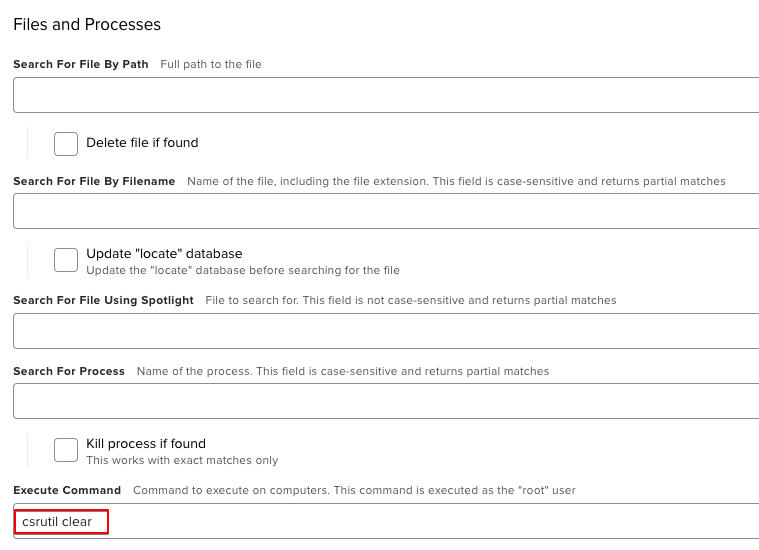
The command will only be applied if we restart the computer. We will set a restart option. I choose to restart immediately if there is no user logged on, so if the user logs off instead of restarting, we still apply the fix.
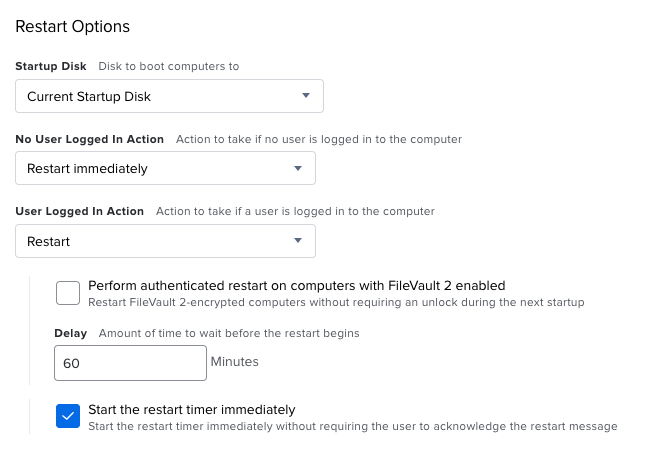
Finally, we will scope it to our smart group.
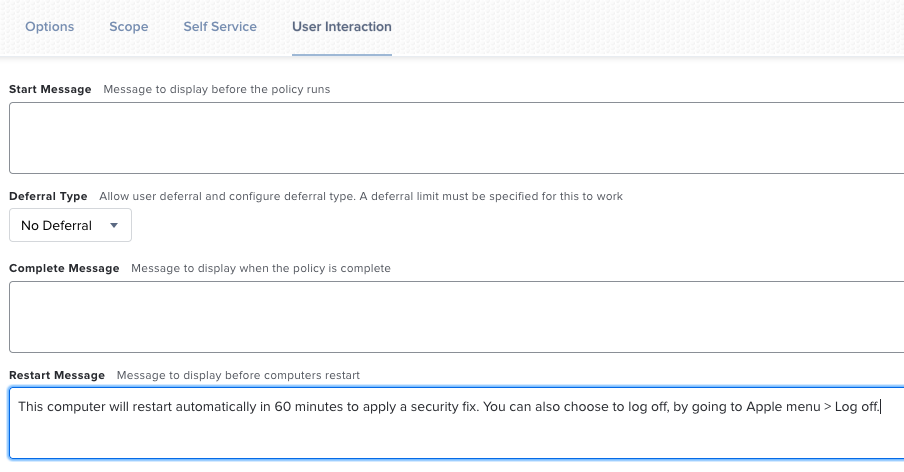
In User Interaction tab, you can define a message displayed when the policy runs, explaining why you’ll restart the computer.
We are now ready. At the next check-in, the machine targeted by our policies will reapply these security measures and will be protected against malicious code.
